Cybersecurity Risks in Power Metering
As cybersecurity for energy management concerns rise worldwide, the potential risk for utilities and commercial/industrial energy metering increases significantly. The need for robust cybersecurity measures to protect energy management systems of all sizes cannot be ignored. One access point to energy management data is through metering communication. To address this risk, among others, the North American Electric Reliability Corporation (NERC) designed the Critical Infrastructure Protection (CIP) standards. The standards are aimed at regulating, enforcing, monitoring, and managing the security of the bulk electric system (BES) in North America. These standards apply specifically to the cybersecurity aspects of BES.
Cyber Secure Metering
Encryption is the basis of cyber secure metering. Encryption takes metering data, for example, usernames and passwords, and changes it into a string of characters that is no longer readable without the correct key. Encryption takes place with complicated algorithms that are transparent to the user of the system.
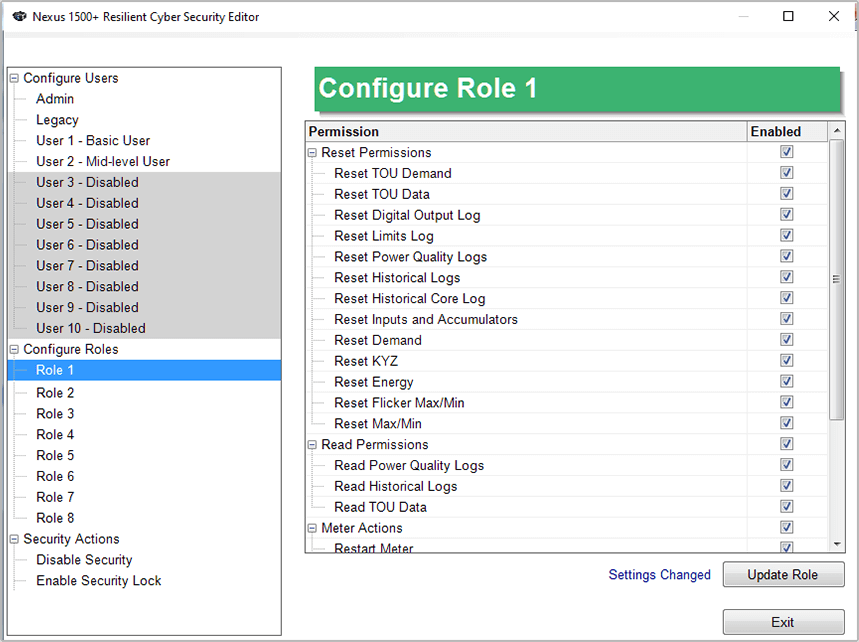
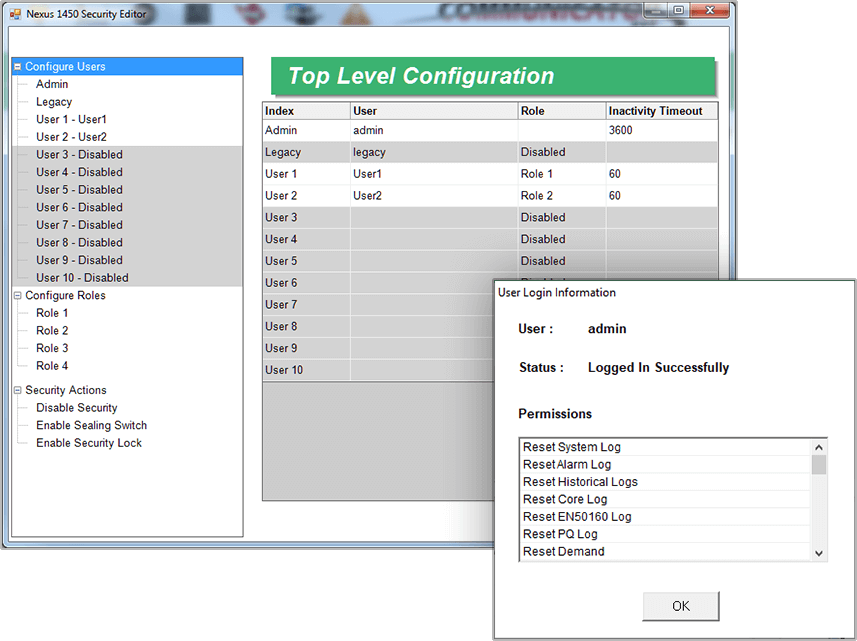
In addition to encryption, cyber secure metering should offer role-based permissions, which enables the setup of multiple users with specific capabilities. For instance, one user may be able to download meter logs, while another may only be able to view real time polling screens. A third user may be able to amend the meter’s configuration, e.g., changing the meter’s clock. There should be an upper level user, or admin, who is able to create users and give them passwords, enable and disable security, and assign roles or permissions to individual users.
Another necessity for cyber secure metering is a digital firmware signature that confirms that any firmware files running in the meter or being uploaded to the meter are valid, authentic files. This is necessary to ensure that malware files are not inadvertently or maliciously uploaded to the meter. That would not only compromise the meter, but risk infection of the entire electrical system.
To be cyber secure, meters should virtually eliminate brute force attacks with password fail timeouts. They should also have physical means, such as seal switches and physical locks, to make remote tampering impossible. The latter is especially important for revenue meters.
EIG’s Line of Cyber Secure Meters
Electro Industries/GaugeTech (EIG) has a proven track record of producing meters with AES encryption-based advanced cybersecurity. AES encryption is one of the NIST approved algorithms for cybersecurity, specified in FIPS 197. One example of this is the Nexus® 1500+ Power Quality meter. The Nexus® 1500+ meter has EIG’s latest Resilient Cyber Security™, which complies fully with utility security requirements. The Nexus® 1500+ meter’s cybersecurity includes:
- AES 128-bit encrypted communication – It is estimated that it would take a supercomputer billions of years to crack a 128-bit encryption key1. The Nexus® 1500+ meter protects passwords, usernames, roles, and rights using AES 128-bit encryption.
- Role-based authorization – The Nexus® 1500+ meter offers multiple roles to restrict access to meter data and configuration. It has an admin level with full rights and up to ten configurable user levels.
- Only the admin level can create user profiles and permissions, usernames, or passwords.
- Only the admin level can enable or disable security for the meter.
- The admin can program expiration dates for passwords to further secure data by periodically setting up new passwords.
- Password fail timeouts – To prevent brute force hacking, in which a system is inundated with multiple password entries in an attempt to identify the correct password, the meter has password fail timeouts. The timeouts will block password entry for a designated period (from one minute to 24 hours) after three consecutive incorrect passwords are entered. This breaks the chain of password hacking.
- The admin level can view any authorized users that are in lockout due to failed password attempts.
- 512-bit digitally signed firmware – A digital signature is an encrypted value, or “key,” attached to a file. Before the firmware can be uploaded to the meter, the file‘s key is decrypted by the public key in the Nexus® 1500+ meter. This ensures that the firmware file is authentic and valid, so that the meter cannot be hacked or infected with malware files.
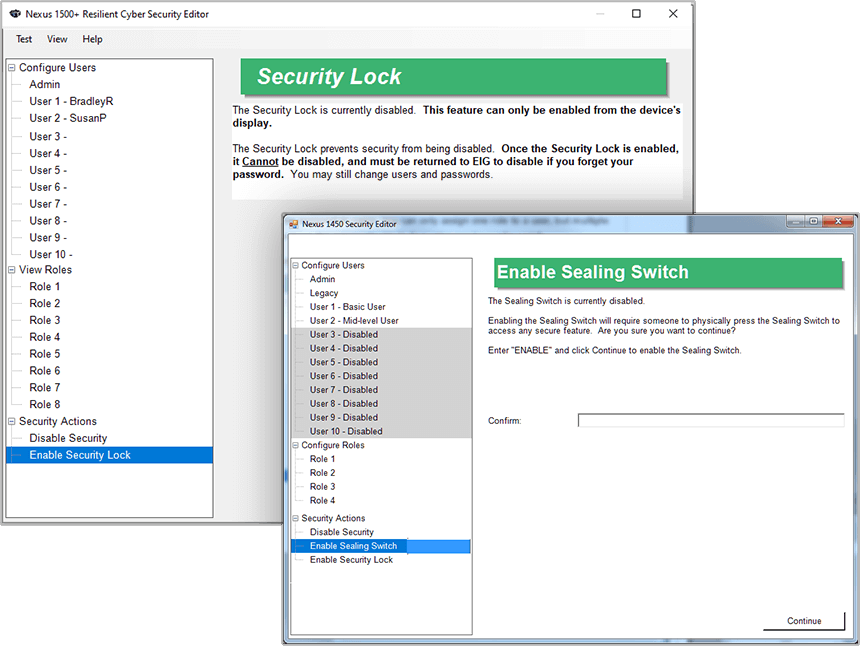
- Security lock – For applications with the most stringent security needs, the admin level user can implement a security lock. This will prevent the security from being disabled, even by the admin. The security lock is implemented in the meter’s firmware and enabled via the meter’s display.
- Sealing switch – The Nexus® 1500+ meter’s sealing switch acts as a physical barrier, requiring a meter button to be pressed in addition to software password entry. This is an added level of security, since the button is located under an area that can be secured with a physical seal and which would indicate tampering if removed.
- Physical seals – The meter’s seals prevent unauthorized access and indicate if tampering has been attempted.
- Anti-tampering System Events log – The System Events log records any actions in the meter, such as password entry, meter resets, log downloads, etc.
In addition to the Nexus® 1500+ meter and the CommunicatorPQA® software, EIG offers the following meters and applications with advanced cybersecurity:
- Nexus® 1450 cyber secure power quality meter with multiport communication.
- Shark® 250 cyber secure power and energy meter.
- Shark® 270 socket and switchboard form revenue meter with cybersecurity.
1 What Is AES Encryption? [The Definitive Q&A Guide], Brett Daniel, March 31, 2021; website link https://www.trentonsystems.com/blog/aesencryption-your-faqs-answered
The Future
As advances are made in cybersecurity encryption, meters used in critical energy applications must be updated to use that latest technology as well. EIG is at the forefront of cyber secure metering and will continue to produce meters and software that provide the cybersecurity our customers, large and small, require to keep their data secure.
Popular Products in Cyber Secure Power Metering
Nexus® 1500+ Meter
Nexus® 1500+ Meter
Nexus® 1450 Meter
Nexus® 1450 Meter
Shark® 250 Meter
Shark® 250 Meter
Shark® 270 Socket or Switchboard Form Meter
Shark® 270 Socket or Switchboard Form Meter
Engineering Services